Managing updates with Intune
These policies get really into the weeds of Windows update types. I would recommend brushing up on Windows Update Types. Currently there are 3 policy types for managing windows updates.
- Update Rings.
- Feature Updates.
- Quality updates.
Update rings
Update rings have been around for awhile. This lets you configure policies to defer updates for a short period of time, and set user experience settings.
Prerequisites
- Windows 1607+
- Editions Pro and up.
- The Microsoft Account Sign-In Assistant (wlidsvc) not set to disabled. This causes Windows Update to not offer feature updates to devices running Windows 10 1709 or later, or Windows 11
- Telemetry configured to required. (In a Windows 10 Device Restriction policy configured under Reporting and Telemetry > Shared Data Usage.)
- Doesn't support win 10 LTSC must use WSUS.
Creating Update rings
To create a new update ring in Microsoft Endpoint Manager: 1.Navigate to the Devices > Windows > Windows Policies > Update Rings
- Click Create Profile + Name the profile
- Add your desired settings.
- Apply the policy to a group or all devices.
-
Done. Easy right? Now lets actually explain some of these settings.
Settings Explanations
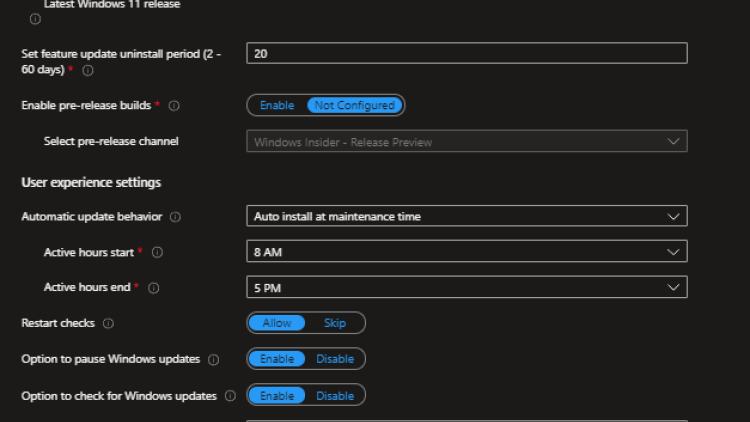
- I'm going to skip over some of the self explanatory ones. Below is a screenshot of all of the update settings you can configure.
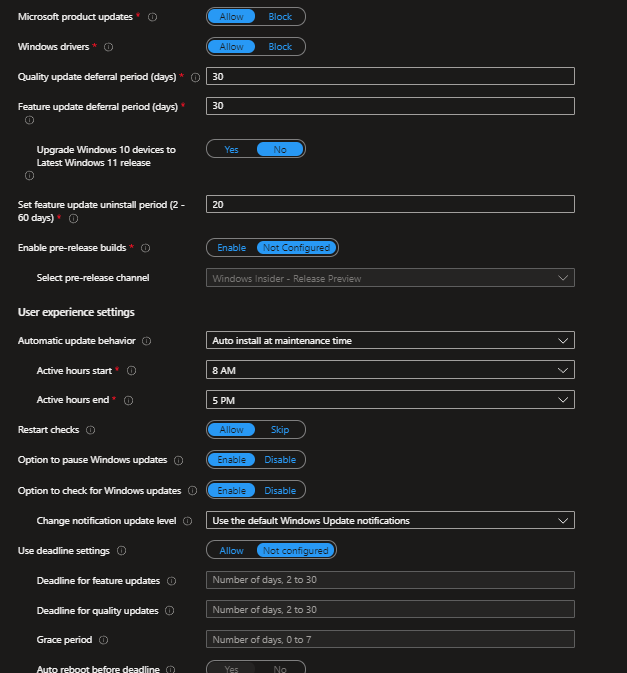
- I'm going to skip over some of the self explanatory ones. Below is a screenshot of all of the update settings you can configure.
- Microsoft Product updates - (Allow updates for office etc)
- Driver Updates - (Download device drivers from windows update)
- Quality update deferral (Days) - Quality updates not be offered until (0-30) days after release.
- Feature update deferral (Days) - Feature updates not be offered until (0-365) days after release.
- Upgrade Windows 10 Devices to latest windows 11 release -
- Set feature uninstall period (2-60 days) - Sets how long before the feature update is baked into the OS permanently.
- Enable Pre-release builds - Enable pre-release for testing quality updates.
User experience settings
Automatic update behavior. (least ⇒ most aggressive)
-
Notify Download - Notifies user to download and does nothing until deadline.
-
Auto install at maintenance time - Downloads + installs outside of active hours if plugged in.
- If restart required notifies for 7 days then forces reboot
-
Auto install and restart at maintenance time - Adds automatic restart outside of active hours.
-
Auto install and restart at scheduled time - Set specific day(s)of week + time for install and reboot. (Default: 3AM - Daily)
- If restart is required attempts with user logged in: 15 minute countdown with Option to delay
-
Auto install and reboot without end-user control - End user not given option to delay.
- Uses Intelligent Active Hours. With this setting enabled you cannot configure the Active hours start and Active hours end setting.
-
Reset to default - Removing update ring policy from a device does not remove settings. This removes previously configured settings.
-
Restart Checks - Prevents reboot if: Battery low, Presentation mode, User present.
-
Option to Pause windows updates - This one isn't nearly as bad as it sounds. The default pause is 7 days (Max 35). After the pause they are required to bring the device to full patch before pausing again.
-
Option to check for windows updates - Allows clicking the Check for Updates button in settings.
-
Change Notification Update Level
- Not configured
- Use the default Windows Update notifications
- Turn off all notifications, excluding restart warnings
- Turn off all notifications, including restart warnings
-
Use Deadline Settings - Sets a hard date for installing and restart. Depending on what update behavior is set to these may or may not come into play. Feature updates and Quality are specified separately.
-
Grace Period - additional time for Windows to try to find device downtime before installing + Restart.
- Useful for when device has been offline for some time. Allows user to user to get some work done before updating.
Auto Reboot before Deadline - Specifies whether a non user initiated reboot can occur before deadline.(outside of active)
Conclusion
What settings you end up using will be highly dependent on your compliance needs, and user behavior. You will need to answer some of the following questions:
- How far can the devices be behind?
- Are your devices mobile or PC devices? PC's can be updated pretty consistently. Laptops can be problematic for users who do not use them frequently or do not leave them plugged in during maintenance windows.
- How likely are the users to follow update and restart notifications?
- Useful for when device has been offline for some time. Allows user to user to get some work done before updating.
Auto Reboot before Deadline - Specifies whether a non user initiated reboot can occur before deadline.(outside of active)
I was planning to include all 3 of the Microsoft Endpoint Manager (Intune) policies in this article but this one is getting a little long. I am going to create a part 2 talk about feature update policies.